个人备案网站做盈利合法吗网站建设费可以走办公费吗
一.简介
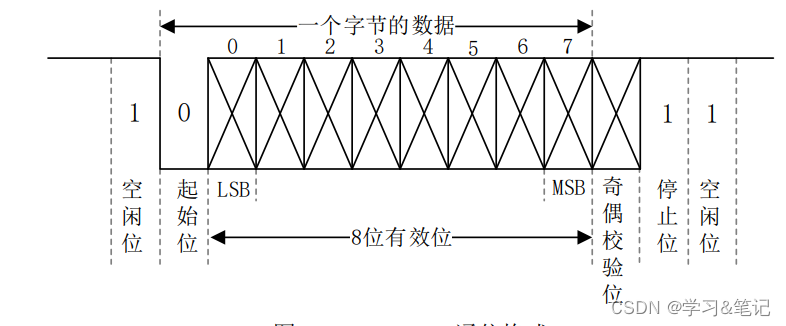
串口全称叫做串行接口,通常也叫做 COM 接口,串行接口指的是数据一个一个的顺序传 输,通信线路简单。使用两条线即可实现双向通信,一条用于发送,一条用于接收。串口通信 距离远,但是速度相对会低,串口是一种很常用的工业接口。
UART 作为串口的一种,其工作原理也是将数据一位一位的进行传输,发送和接收各用一 条线,因此通过 UART 接口与外界相连最少只需要三条线:TXD(发送)、RXD(接收)和 GND(地 线)。
uart数据格式:
二.硬件原理

三.驱动部分
在Linux kernel 4.4和Linux kernel 4.19中,使用8250串口通用驱动,以下为主要驱动文件:
drivers/tty/serial/8250/8250_core.c # 8250串口驱动核心
drivers/tty/serial/8250/8250_dw.c # Synopsis DesignWare 8250串口驱动
drivers/tty/serial/8250/8250_dma.c # 8250串口DMA驱动
drivers/tty/serial/8250/8250_port.c # 8250串口端口操作
drivers/tty/serial/8250/8250_early.c # 8250串口early console驱动
menuconfig配置:
Device Drivers --->Character devices --->Serial drivers --->
dts配置:
uart2: serial@fe650000 {compatible = "rockchip,rk3568-uart", "snps,dw-apb-uart";reg = <0x0 0xfe650000 0x0 0x100>;interrupts = <0 117 4>;clocks = <&cru 287>, <&cru 284>;clock-names = "baudclk", "apb_pclk";reg-shift = <2>;reg-io-width = <4>;dmas = <&dmac0 2>, <&dmac0 3>;pinctrl-names = "default";pinctrl-0 = <&uart1m0_xfer>;status = "okay";};
&uart1 {pinctrl-0 = <&uart1m0_xfer>;status = "okay";
};四.波特率配置
UART波特率 = 工作时钟源 / 内部分频系数 / 16
目前,UART驱动会根据配置的波特率大小自动去获取需要的工作时钟频率,可以通过以下命令查询到UART工作时钟频率:
cat /sys/kernel/debug/clk/clk_summary | grep uart
五.串口查看工具SecureCRT



 串口能连上终端,有信息打印。
串口能连上终端,有信息打印。
